The home addresses and cell phone numbers of members of Iran’s IRGC, its Basij militia and police forces who are oppressing and attacking Iranian protesters are being published on the darknet to enable the public to seek out revenge, The Jerusalem Post has learned.
Israeli cyber intelligence firm Deep Void, whose founders have a background in Israeli intelligence, has revealed the phenomenon in which Iranian dissidents are using the darknet, a shadow realm within the Internet, to fight back against the ayatollahs’ foot soldiers, who during past protests could attack protesters and then disappear into anonymity.
According to Deep Void CEO Raphael Saedian and CTO Teodor Borozdin, there are signs that the new darknet initiative is bearing fruit and growing in a way that could eventually alter the strategies of both the Iranian regime and the anti-regime protest movement.
The protests, which started around two and a half months ago after Iran’s morality police tortured and murdered Mahsa Amini for what they deemed was insufficient modesty, are emerging as possibly the greatest challenge to the ayatollahs’ iron grip on the country in over a decade.
Deep Void’s findings indicate that the third phase of the digital battle has started, in which protesters have become sophisticated enough to use the darknet and other tools to track and retaliate against their oppressors.
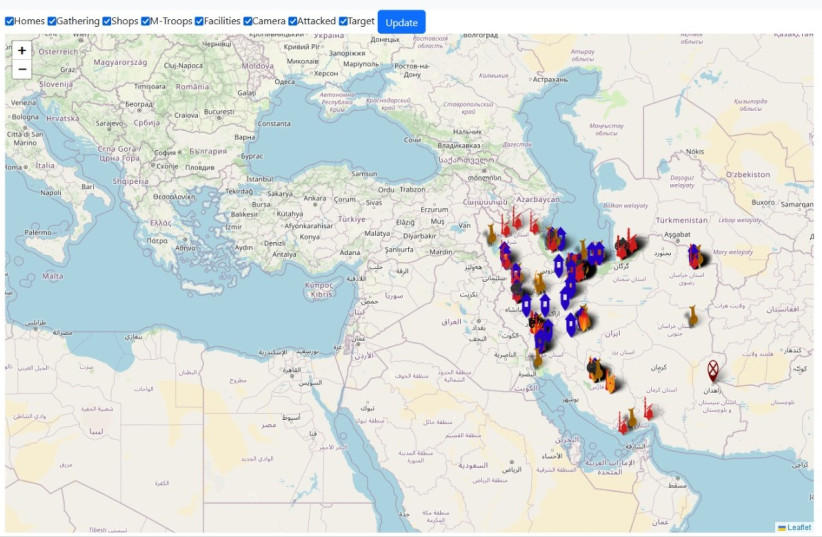
The cyber intelligence firm provided a number of specific examples to show how digital dissidents are fighting back.
Digital dissidence on the Darknet
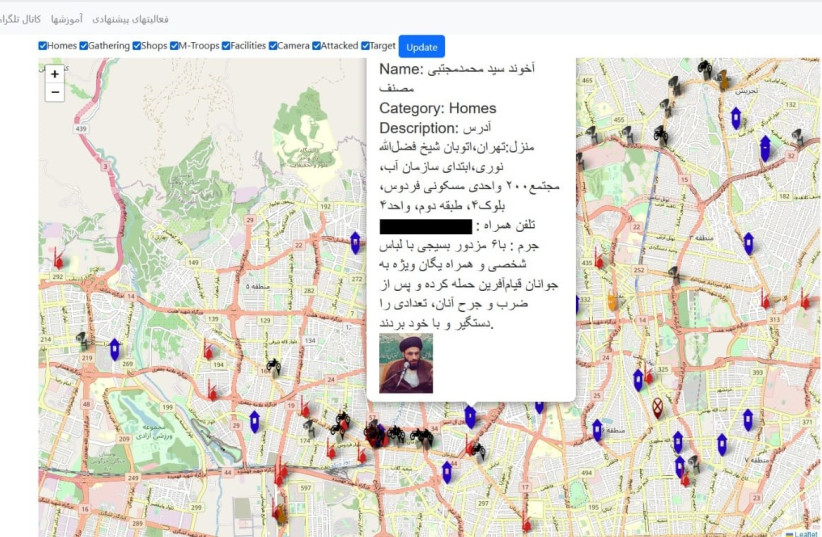
One photo posted on the darknet site names Akhund (meaning a religious person) Syed Muhammad Mujtaba Musanaf, noting that he participated in the violent arrest of local youth protesters alongside the Basij militia.
Another photo shows the location of a specific mosque that Basij troops are using to rest and reorganize.
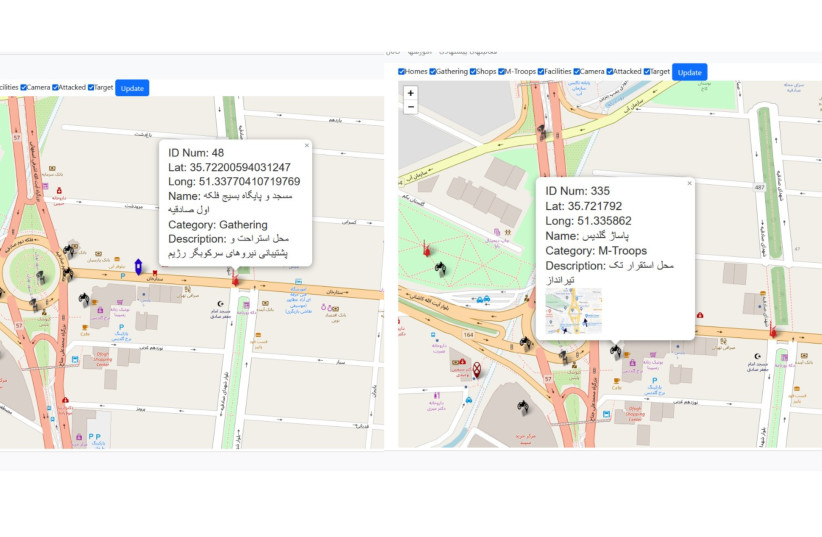
Yet, another photo shows a mall that was being used by a sniper as a spot for targeting protesters.
In addition, a photo notes a man named Jalal Hemat Alahi from Isfahan was attacked with a Molotov cocktail after violently dispersing protesters.
Immediately after the Molotov cocktail attack, cameras were installed around his house.
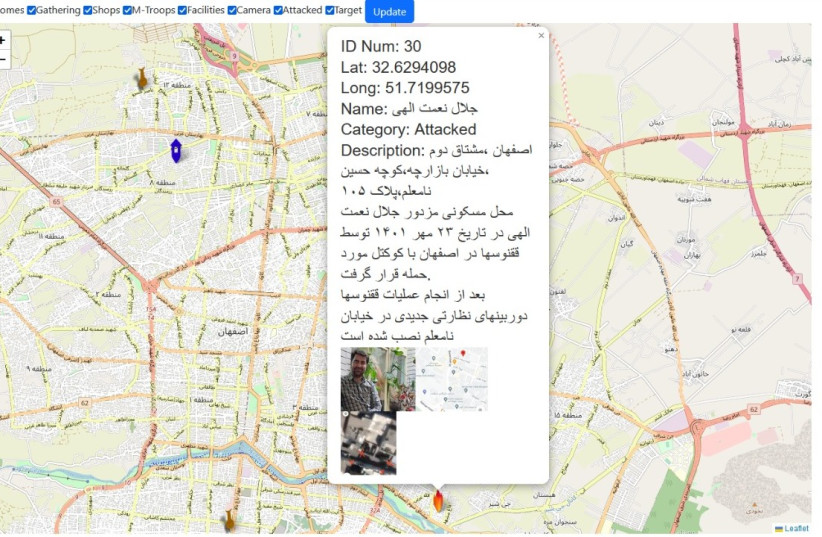
The level of detail included in these posts could be used by protesters to surprise-attack Basij when they’re resting and their guard is down, to avoid being hit by a sniper or to be prepared to disable cameras if they want to attack Alahi again.
In a way, the site is providing operational intelligence to any protester in the general public who wants to retaliate against those oppressing him, when the foot soldiers of the regime do not have superior numbers and firepower as they often do on the street.
There is another photo that shows a huge volume of sites in Iran about which the darknet site is providing information.
It is unclear how far this will go or transformative this phenomenon will become, but Deep Void viewed the development as highly significant.
What is Deep Void?
Deep Void specializes in “providing intelligence and cyber intelligence based on unique know-how and experience at darknet, deep web, clearnet and social media,” the company website states. “Our core competence is with in-depth and intimate acquaintance with different cultural and linguistic variance.”
Both Saedian and Borozdin are now applying skills they learned during their years in the Israeli intelligence community to open-source information to help mostly governments and law enforcement agencies to combat ransomware, with counterterrorism and with anti-crime intelligence generally.
Saedian told the Post that their clients include both long-time friends of Israel and countries that have become allies of Israel much more recently – likely a reference to various moderate Sunni countries.
Generally, the protesters are using TOR, or “The Onion Router,” a network that bounces digital traffic through random nodes, wrapping it in encryption each time. This also makes it difficult for people or groups, such as the Iranian regime, to track.
TOR is part of the so-called “dark web,” a layer of the Internet that isn’t searchable via Google or accessible via standard browsers.
